Technology is evolving rapidly, and people blindly use electronic gadgets and software. It is hard to see the negative side of technology when the positive side already influences you. The dark side of technology includes malware, viruses, cybercrimes, sniffing, etc.
Electronic eavesdropping is another technology bug involving a middleman listening to everything through your electronic gadgets. Getting attacked by a virus in a computer is what everyone knows. But people need to become more familiar with the eavesdropping concept. You must go for professional bug sweeping when you observe anyone watching you through your electronic gadgets.
In this write-up, you will learn more about electronic eavesdropping and how a criminal unknowingly attacks you. If you know the bright side of technology, it is a must to know it is dark before it gets too late.
Page Contents
About Eavesdropping

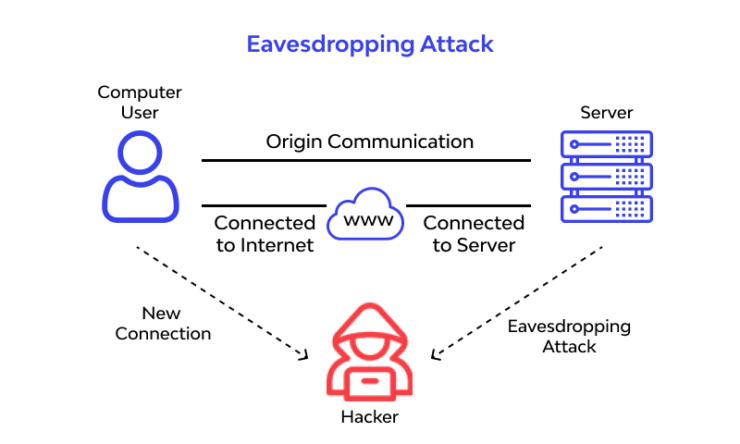
It is a digital attack involving an eavesdropper who can listen to the communication between two devices. Data transmission occurs in phones, computers, fax machines, voice assistance devices, etc. You can call this attack snooping.
The tracker can get into the open network and get all the information. It is hard to detect and track these eavesdroppers. You can protect yourself by preventing them. There is no way to find and punish them. You must be cautious while using any electronic device or operating them in a secure network.
Different Electronic Eavesdropping Forms

This digital attack can take place in different forms. But you must be aware of the common ones.
Audio
The attacker can put your audio devices on surveillance by using your microphones. Through Infrared or UV spectrum, the tracker can listen to your private conversations. The microphone is attached to many music gadgets or radios, and unknowingly, you can leak confidential data to these attackers.
Video
The attacker does video surveillance when small cameras are hidden in different corners to record all your activities. The cameras can be hidden in sensitive areas, and you will not know about them.
Signal Intercepts
The attacker can find prey on open networks, i.e., local Wi-Fi connections. It can happen during any call or when you use an unknown wireless connection.
Malware
Any malware or harmful viruses can enter your device in many ways. The attacker can access all the confidential files of your computer through malware. Unknowingly, you will open links sent by the criminal, and all your data will get leaked.
Weak Passwords
If you have set weak passwords for your accounts, a hacker can easily open them and access crucial details. Many online tools can crack passwords by using brute force or other methods. It is easy to steal sensitive information from your account and misuse it.
Eavesdropping Types
Active
In an active state, the attacker tries to modify the message content. If two individuals are communicating with each other, then the third person can read the complete conversation.
When one person sends a message, the attacker can modify it before receiving it on another side. It is hard to determine the involvement of the third person. Both the message sender and receiver are unaware of such modifications.
Passive
In the passive state, the attacker copies the message from an unencrypted network without giving any hint to anyone. There is no modification in the message, and everything seems normal. The hacker can misuse the copied information and ruin one’s life.
Eavesdropping Attack Impacts
Privacy Loss: Anyone who can steal confidential information from your private accounts can leak or misuse it. You will lose your privacy, and it can also ruin your reputation.
Identity Theft: When the attacker can access your account credentials, you will lose your identity as another person will now handle your account.
Money Loss: The attacker can steal information and money from your bank account. You can also receive threatening messages for ransom, making you lose a large sum.
Preventive Measures
Create Strong Passwords
It is hard to crack strong and long passwords. While creating a password, you must add numbers, alphanumeric, alphabets, symbols, etc. Your password should be long, so it takes months for any application to crack.
Odd Functioning of Electronic Devices
Something must be wrong if your electronic devices, like television, music system, etc., are interfered with or make odd noises. Maybe someone is trying to access your devices and disrupt your privacy. You must keep checking the functioning of the devices so that no one can track you.
Avoid Using Open Networks
You should avoid using open networks that are available outside your place. You must disconnect the Wi-Fi connection in your mobile or laptop to avoid connecting it automatically. It is important to secure your Wi-Fi connection with a strong password so no one can access it.
Use Encryption
You must use encryption while making confidential conversations. It is hard for an eavesdropper to get into an encrypted network and steal any information. It takes years to decode any message if transmitted on an encrypted network.
Download Apps from Official Site
Many people download applications from unknown sites on computers, mobiles, or smart TVs. But it is better to use reputed or official sites for downloading software. No malware or harmful viruses are attached to these sites, and they will not affect your device.
Keep Your System Updated
If your device is not updated, it becomes more prone to cyberattacks. You must keep the system updated to secure your device. Whenever you see the update status on your device, you must update your system.
The Bottom Line

Eavesdropping is a common way to access the confidential details of any electronic device user. The attacker can get into the network and steal the data transmitted from source to receiver. It is hard to detect the eavesdropper, but you can prevent getting trapped in such a situation by following preventive measures.

